The Lure of Phishing: Why It’s Effective
Phishing, at its core, is about deception and trust exploitation. Attackers masquerade as trustworthy entities to trick victims into revealing confidential information. Here’s why phishing has become the go-to strategy for cybercriminals:
-
Cost-effective: Crafting a phishing email costs next to nothing. Compared to the potential financial gain, the initial investment is minimal.
-
Adaptability: Phishing schemes can be quickly modified to bypass new security measures, keeping them one step ahead of many prevention systems.
-
High Success Rate: Social engineering leverages human psychology, which often proves more vulnerable than technology. Fear, urgency, and curiosity are powerful motivators that phishers exploit masterfully.
Anatomy of a Phishing Attack
Phishing attacks come in various forms, each tailored to maximise the chances of success. Let’s dissect a common scenario:
-
The Bait: An email appears in your inbox, seemingly from your bank. It warns you of suspicious activity on your account and urges you to click a link to verify your identity.
-
The Hook: The link directs you to a counterfeit website that looks identical to your bank’s official site. Here, you are asked to input your login credentials.
-
The Catch: Once you enter your information, it’s captured by the attackers, who now have access to your real bank account.
Real-Life Scams and Frauds
The Notorious “Nigerian Prince” Scam
One of the most infamous phishing scams is the Nigerian Prince scam, also known as the 419 scam. Victims receive an email from a supposed Nigerian prince who needs help transferring a large sum of money out of his country. In return for their assistance, the victim is promised a hefty reward. However, to facilitate the transfer, they must first provide their bank details and pay certain fees. Once these fees are paid, the scammers disappear, leaving the victim out of pocket and potentially with compromised bank information.
The Facebook Data Breach Phish
In 2018, Facebook users were targeted in a phishing campaign where they received emails mimicking official communication from Facebook. The emails warned users that their accounts had been compromised and urged them to click on a link to secure their accounts. The link led to a fake Facebook login page where the victims’ credentials were stolen.
The COVID-19 Relief Fraud
During the COVID-19 pandemic, phishing attacks surged, exploiting people’s fears and uncertainties. One prevalent scam involved emails purporting to be from government agencies offering financial relief. Victims were directed to provide personal information and bank details to receive their stimulus checks, only to find their information used for identity theft.
Psychological Manipulation: The Heart of Social Engineering
Phishing attacks are so effective because they tap into core human emotions and psychological triggers. Let’s delve into some of these manipulative tactics:
-
Urgency and Fear: Phishers create a sense of urgency to prompt immediate action. Messages often include warnings about account suspensions or unauthorised transactions, pushing victims to act quickly without verifying the source.
-
Authority: Emails or messages appear to come from authoritative figures or organisations, such as banks, employers, or government agencies, making the request seem legitimate.
-
Curiosity: Sometimes, the lure is purely curiosity-driven, like a subject line that reads, “You’ve won a prize!” or “Check out these photos of you!”
-
Greed: Promises of financial gain or easy money often entice victims to overlook the risk and bite the bait.
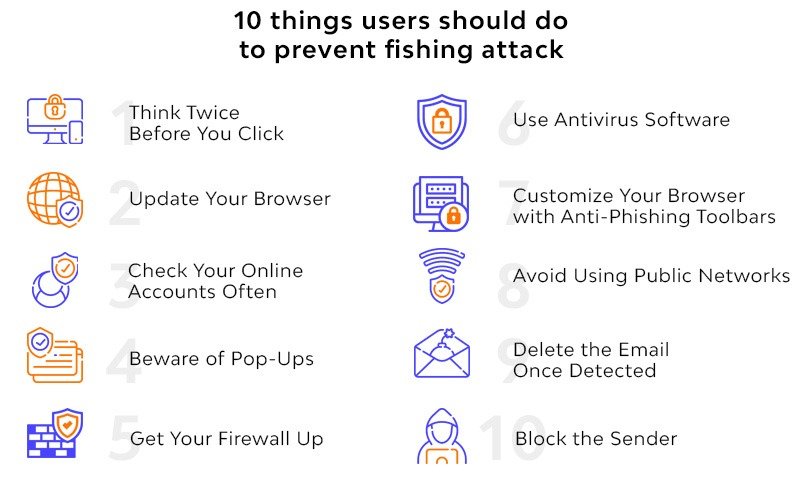
Protecting Yourself: Tips and Tricks
While phishing tactics are sophisticated and constantly evolving, there are steps you can take to protect yourself
Phishing in the Modern Era: Adapt or Get Hooked
Phishing tactics continue to evolve, with attackers becoming more sophisticated in their methods. The rise of artificial intelligence and machine learning has given phishers new tools to craft even more convincing emails and messages. For instance, AI can be used to scrape social media for personal details, allowing phishers to create highly personalized and targeted attacks.
Case Study: The Business Email Compromise (BEC)
One of the most damaging forms of phishing is the Business Email Compromise (BEC). In a BEC attack, phishers infiltrate a company’s email system and impersonate executives or trusted employees. They then instruct other employees to transfer funds or provide sensitive information. BEC attacks have cost businesses billions of dollars globally.
Example: The FACC Fraud
In 2016, FACC, an aerospace company, fell victim to a BEC attack that cost them $47 million. The attackers impersonated the CEO and instructed an employee to transfer a large sum of money to an account under their control. By the time the fraud was discovered, it was too late to recover the funds.
The Role of Technology in Combating Phishing
Technology companies are continually developing new tools to detect and prevent phishing attacks. Here are a few cutting-edge solutions:
-
Advanced Email Filters: These filters use machine learning algorithms to identify and block phishing emails before they reach your inbox.
-
Phishing Simulations: Organisations can run simulated phishing attacks to train employees on how to recognise and respond to phishing attempts.
-
AI and ML—artificial intelligence and machine learning—are being used to analyse patterns and detect phishing attempts more accurately.
Conclusion: Staying One Step Ahead
Phishing remains a significant threat in the digital landscape, driven by the cunning use of social engineering. The best defense is a combination of technology, awareness, and vigilance. By understanding how phishing works and staying informed about the latest tactics, you can protect yourself and your organization from falling prey to these cybercriminals.
Stay alert, stay informed, and always think before you click.
References
By staying vigilant and educating yourself about the evolving tactics of phishers, you can navigate the treacherous waters of the internet with confidence and security.